
Investigations are currently carried out by the financial technology organization Finastra regarding the reported widespread theft of data from its internal system for transferring files, as informed by KrebsOnSecurity. Finastra, a provider of software and services to 45 of the leading 50 banking institutions globally, notified its clients of the security breach after a cybercriminal started offering over 400 gigabytes of data allegedly taken from the company.

Finastra, headquartered in London, operates in 42 different countries and disclosed revenues of $1.9 billion in the previous year. The company has a workforce exceeding 7,000 individuals and serves about 8,100 financial organizations across the globe. A significant aspect of Finastra’s day-to-day operations involves handling large amounts of digital files that contain instructions for bank transfers on behalf of its customers.
On November 8, 2024, Finastra informed its banking customers that on November 7, its security unit identified suspicious activities on the company’s internally hosted platform for file transfers. Additionally, Finastra mentioned to its customers that an individual had initiated selling substantial quantities of files allegedly obtained from its systems.
“On November 8, a malevolent entity communicated on the dark web stating to possess data extracted from this platform,” as stated in Finastra’s disclosure, a document shared by a source linked to one of the client firms.
“Customer operations, systems of our clients, and Finastra’s capability to support our clients remain uninterrupted,” the notice further mentioned. “We have implemented an alternative secure platform for file sharing to guarantee continuity, with ongoing investigations in place.”
Nevertheless, the notification to clients acknowledges that the unauthorized intruder successfully retrieved or “exfiltrated” an undisclosed amount of client information.
“The malevolent entity did not introduce malware or manipulate any customer files within the system,” the notification states. “Moreover, no files other than the extracted ones were actually accessed or viewed. Our current focus is on ascertaining the extent and characteristics of the data contained within the extracted files.”
In a written response to queries concerning the event, Finastra mentioned that they have been “actively and transparently addressing inquiries from our clients and informing them about what we have and have not yet established regarding the posted data.” The company also circulated an updated communique to its clientele, indicating that while the investigation into the root cause is ongoing, “preliminary evidence suggests that compromised credentials are involved.”
“Additionally, we have been providing Indicators of Compromise (IOCs) and our Chief Information Security Officer has been directly engaging with the security squads of our clients, offering progress updates on the examination and our eDiscovery process,” the statement continued. Here are the further details shared:
“Regarding eDiscovery, we are assessing the data to identify the specific customers affected, while concurrently evaluating and communicating which of our products are not reliant on the specific edition of the SFTP platform that was compromised. The impacted SFTP platform is not universally used by all customers and is not the primary platform for exchanging data files among Finastra and its clients for a wide array of our products, hence we are striving to promptly exclude affected customers. Nevertheless, this process is time-intensive given our numerous major clients utilizing various Finastra products across different business segments. Accuracy and transparency in our communications remain our primary focus.
Of utmost importance, for any impacted clients, we will be reaching out and collaborating directly.”
On November 8, a cybercriminal under the alias of “abyss0” posted on the cybercrime community BreachForums in English, declaring that they had obtained files belonging to some of Finastra’s prominent banking customers. The data auction did not specify an initial or fixed price, but advised interested buyers to contact them via Telegram.

abyss0’s sales thread on BreachForums from November 7 displayed several screenshots of the file directories from various Finastra clients. Image: Ke-la.com.
As per the data from the cyber intelligence platform Ke-la.com, abyss0 initially tried to peddle the allegedly stolen data from Finastra on October 31, with the earlier sales thread not identifying the targeted company. Nonetheless, it did mention several eminent banks that are customers of Finastra, as highlighted in the November 8 post on BreachForums.
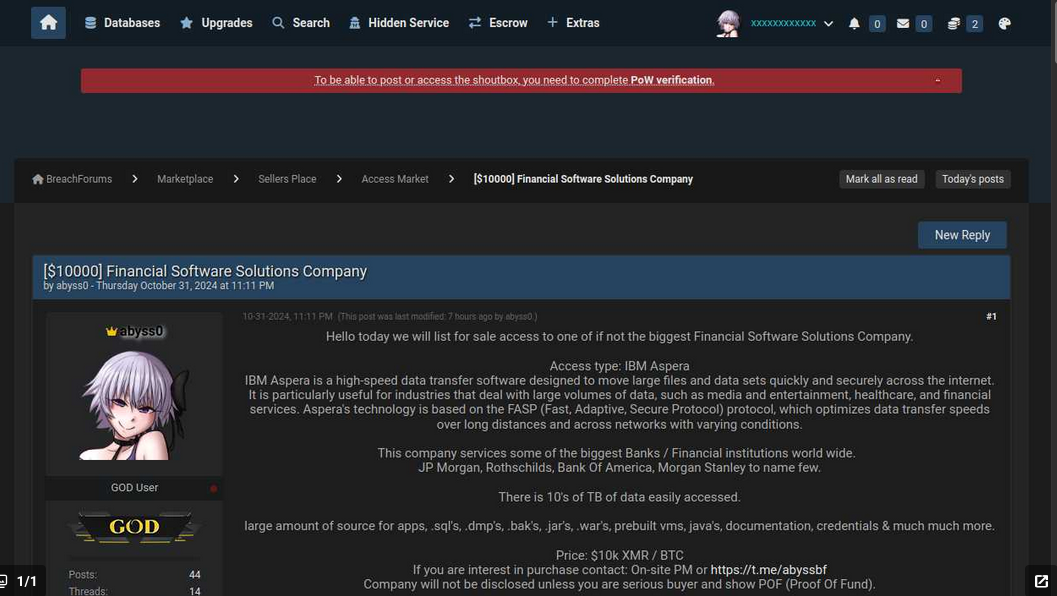
The initial post by abyss0 on October 31, advertising the sale of data from various prominent banks that are clients of a major financial software firm. Image: Ke-la.com.
The sales thread from October also showcased an opening bid of $20,000, which was later lowered to $10,000 by November 3. A review of abyss0’s posts on BreachForums reveals their efforts to sell databases stolen from numerous breaches advertised over the past half-year.
The potential timeline of this breach suggests that abyss0 accessed Finastra’s file sharing system at least a week prior to the company’s discovery of suspicious activity, indicating that the activity detected on November 7 may have been linked to the intruder returning to pilfer more data.
Possibly abyss0 secured a buyer who financed their prompt retirement. The disappearance of this individual leaves many questions unanswered. The Telegram account provided by abyss0 in the sales thread appears to have been removed or deactivated. Furthermore, abyss0’s profile on BreachForums is no longer accessible, and all sales threads associated with it have disappeared.
It seems less likely that Telegram and BreachForums simultaneously terminated abyss0’s access. The most plausible explanation is that something unsettled abyss0, leading to their abandonment of various ongoing sales endeavors and a meticulously curated cybercrime persona.
Back in March 2020, Finastra encountered a ransomware assault that disrupted several of the company’s fundamental operations for a number of days. According to reports from Bloomberg, Finastra managed to rebound from that incident without paying the ransom demanded.
This narrative continues to evolve. Timestamps will be added to denote updates. Should you possess additional insights regarding this incident, please contact krebsonsecurity@gmail.com or protonmail.com.










