Is Australia’s Public Sector Prepared for a Significant Cyber Security Incident?

A recent investigation into the readiness of Australian Federal Government entities in terms of cyber security has highlighted deficiencies in their preparedness for cyber attacks or major data breaches, leading to a renewed focus in 2024 on enhancing their cyber resilience.
In a report released in 2024, an evaluation of two government agencies, Services Australia and AUSTRAC, revealed that these agencies are inadequately prepared to bounce back from a substantial cyber assault. Meanwhile, a comprehensive survey conducted across government agencies earlier found gaps in the maturity of cybersecurity measures in some areas.
The Cyber Security Strategy for the Australian Government 2023-2030 emphasized the importance of the Federal Government aligning its standards with those of the industry. Furthermore, in 2024, there is an emphasis within the Australian Signals Directorate on enhancing cybersecurity skills within government entities.
Unsuitable Australian Government Entities for the Escalated Cyber Threat Environment
Australian public sector organizations are prime targets for malicious cyber activities due to the sensitive data they possess. For example, the Australian Taxation Office disclosed in 2024 that it faces 4.7 million attacks per month owing to the massive 50 petabytes of data it manages. In another instance, the compromising of the South Australian super fund operator Super SA in 2023 led to unauthorized access to a significant number of individuals’ data.
Incidents Encountered by Australian Government Entities in 2022-23
Official data based on incidents reported to the Australian Signals Directorate indicates that government agencies remain attractive targets for cybercriminals, with a high volume of cybersecurity incidents occurring. In the period of 2022-2023:
- Approximately 31% of cybersecurity incidents reported to the Australian Signals Directorate originated from Australian Government entities.
- Over 40% of these incidents comprised of coordinated low-level malicious cyber assaults targeted at federal government bodies, government-shared services, or critical infrastructure under regulation.
- Ransomware emerged as a prominent cybercrime threat, posing significant risks not only to Australian Government entities but also to businesses and individuals.
SEE: Will Australia ever overcome the shortage of cyber security skills?
The Present Cyber Security State of Government Entities
The 2023 Cyber Security Posture Report from the ASD, which evaluated the maturity levels of all government bodies, indicated that “the overall maturity level across entities remained low in 2023.” The report revealed:
- 25% of entities self-evaluated at Maturity Level Two across the ASD’s Essential Eight mitigation strategies. The Essential Eight framework includes four maturity levels, with Maturity Level Zero being the lowest and Level Three representing the best practices.
- Most public sector entities — 71% of them — self-assessed at Maturity Level Two for the Essential Eight mitigation strategy of “Regular backups,” suggesting potential challenges in recovering from significant cyber incidents.
- Just 82% of entities possessed an incident response plan, though this indicated an improvement from 2022. Among these entities, 90% reported that their plan had been last updated within the past two years, and 69% indicated that it had been activated at least once every two years.
Prior audits conducted by the Australian National Audit Office on public sector entities, including the Australian Federal Police, Australian Taxation Office, and Department of Foreign Affairs and Trade, also highlighted “low levels of cyber resilience in entities.”
AUSTRAC and Services Australia Indicate Cyber Security Deficiencies
A report by ANAO on incident management related to cyber security at Services Australia and AUSTRAC in June 2024 identified their measures as only “partially effective,” indicating that neither entity is adequately positioned to ensure continuity of business or recovery from significant cyber security incidents.
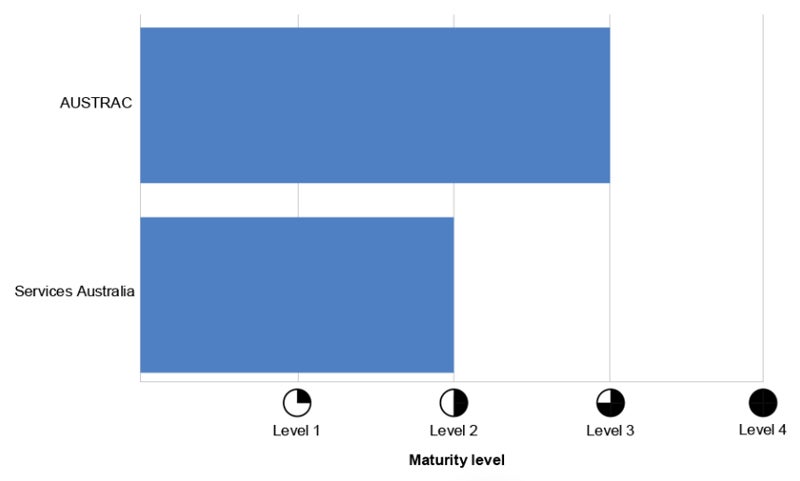
Services Australia, specializing in providing services and payments to citizens, and AUSTRAC, responsible for enforcing against misuse of the financial system for criminal purposes, manage valuable economic, commercial, and personal information, and are categorized as national security or critical infrastructure.
AUSTRAC
As per the ANAO report, AUSTRAC’s protocols supporting incident recovery processes lacked considerations for security testing of backup solutions and did not outline the systems, applications, and servers that support critical business processes.
Moreover, it did not articulate CISO responsibilities — its approach to continuous monitoring and improvement reporting — nor set clear deadlines for reporting. Moreover, the organization lacked an event logging policy and failed to document the analysis of all cyber security events, which goes against ASD guidelines.
SEE: CISOs in Australia advised to closely examine data breach risks
Services
Australia
Services Australia demonstrates only partial effectiveness in crafting cyber security incident management procedures, lacking a documented strategy for threat and vulnerability assessments. Moreover, there is an absence of defined timelines for triage and escalation, as well as a structured approach towards investigations.
While the agency has partly implemented efficient recovery protocols, such as routine backups, its plans inadequately cover all systems and applications that support critical business functions. Notably, the agency does not conduct tests to verify the recoverability of these backups.
What comprises the Australian national cyber security strategy?
Acknowledging the imperative for enhanced cyber security preparedness and resilience among agencies, the Australian government emphasizes the importance of Cyber Security Strategy 2023-2030. In this strategy, the government highlights its obligations as a custodian of critical infrastructure and as a guardian of sensitive information vital to Australia’s populace, economy, and national security, stating that “the government must adhere to the same stringent standards it sets for the industry.”
As part of this strategic vision, the government commits to:
- Enhancing the cyber readiness of government departments and organizations.
- Identifying and securing vital systems across the government spectrum.
- Elevating the cyber competencies of the Australian Public Service.
The ASD has announced its involvement in bolstering security measures at government agencies in 2024 through increased funding. This initiative involves the integration of enhanced technical capabilities within departments and the provision of expert assistance to reinforce agencies’ defense mechanisms against cyber adversaries.
Rising Expectations from the Private Sector Regarding Public Sector Security Standards
The private sector eagerly anticipates enhancements in cyber security within the public sector.
In a recent submission to the government concerning proposed cyber security legislative reforms, The Technology Council of Australia, representing the technology sector, urges the government to enhance and safeguard its information security protocols and practices. This is crucial to ensure that data shared by private sector entities with the government through mandatory cyber incident information sharing processes is transmitted through secure environments and channels.
Amazon Web Services recommended that the government officially include its critical infrastructure and “Systems of Government Significance” within the purview of the Security of Critical Infrastructure Act or a similar legislative framework.
“Such an action would establish essential, enforceable standards for the government,” AWS remarked, “signaling to the industry that the government considers itself an equal stakeholder in the nation’s cyber fortification efforts.”






