Functioning in ‘kernel-space’ – the most authoritative layer of an operating system, with direct entrance to memory, hardware, resource management, and storage – is critically crucial for security products. It empowers them to supervise ‘user-space’ – the non-privileged environment where applications operate – and safeguard against malware that runs in that environment, even when it attempts to avoid discovery. Nevertheless, kernel access also gives security products the ability to counter more subtle threats within the kernel itself. As previously mentioned, for instance, some threat actors use BYOVD (Bring Your Own Vulnerable Driver) attacks, or endeavor to get their own malicious drivers cryptographically signed, to access kernel-space and exploit that heightened level of access.
Yet, from a security perspective, operating in kernel-space presents its own dangers. An incorrect move in this environment – such as a faulty update to a kernel driver – can lead to failures. If the concerned driver initiates at boot time, when the operating system initially boots, that might result in prolonged consequences, potentially necessitating affected hosts to be booted in a recovery mode to handle the issue and allow the systems to boot normally.
Sophos’ Intercept X Advanced solution utilizes five nucleus operators as of release 2024.2. All operators are thoroughly tested* with relevant flags activated and deactivated, and delivered with new flags disabled. (Sophos Intercept X and Sophos Central utilize feature flags to gradually introduce new features. Feature flags are implemented through Sophos Central. Fresh features are usually ‘guarded’ by feature flags – turned off unless the flag is activated – to enable the gradual deployment of the feature and possible revisions before broader activation.)
In this piece, for the sake of openness, we will delve into what those operators are, their functions, startup times, how they are authenticated, and their inputs. We will also explore some protective measures we have established around these operators to diminish the disruption risk (such as phased rollouts, as mentioned earlier; an example of this will be provided later in the article), and the alternatives accessible to customers regarding their configuration. Additionally, it is noteworthy that Intercept X Advanced and all its constituents, including the nucleus operators, have been a part of an external bug bounty program since December 14, 2017; we encourage scrutiny through external bug bounty submissions, and we foster a collaborative relationship with the research community.
* ‘Testing’ encompasses various internal testing methods, which include tools and verifiers provided by Microsoft
The subsequent table furnishes a concise summary of the five nucleus operators incorporated in Intercept X Advanced release 2024.2.
| Operator | Version | Type | Initialization Method | Authenticated By Microsoft? | Authentication | Explanation |
| SophosEL.sys | 3.2.0.1150 | Kernel Operator | Early-Launch Boot Start | Yes | ELAMP* | Sophos ELAM operator: capable of preventing execution of malicious boot start operators |
| SophosED.sys | 3.3.0.1727 | File System Operator | Boot Start | Yes | WHCP+ | The primary Sophos anti-malware operator |
| Sntp.sys | 1.15.1121 | Network Filtering Operator | System Start | Yes | WHCP+ | Sophos Network Threat Protection operator |
| Hmpalert.sys | 3.9.4.990 | File System Operator | System Start | Yes | WHCP+ | Sophos HitmanPro.Alert operator |
| SophosZtnaTap.sys | 9.24.6.3 | Network Filtering Operator | On Demand | Yes | WHCP+ | Sophos Zero Trust Network Access (ZTNA) Tap operator |
Table 1: A summary of the nucleus operators in Intercept X Advanced 2024.2
* Microsoft Windows Early Launch Anti-malware Publisher
+ Microsoft Windows Hardware Compatibility Publisher
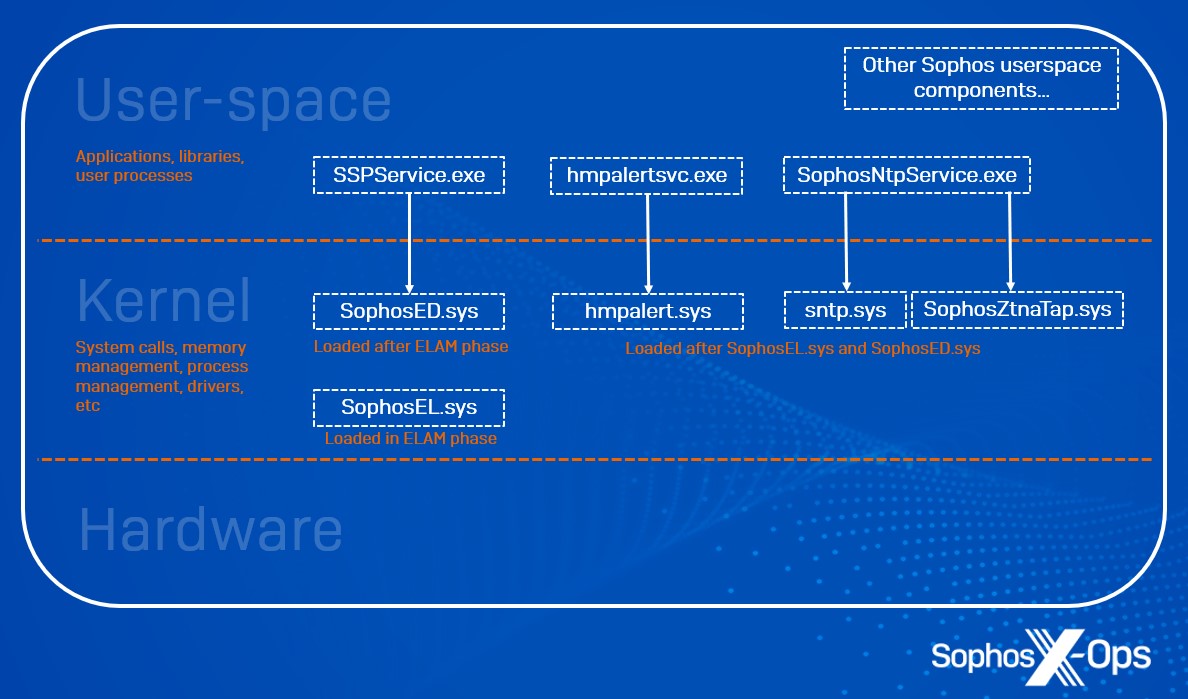
Figure 1: A conceptual portrayal of user-space/kernel boundaries and the areas where Intercept X Advanced components function
Operation: SophosEL.sys is the Sophos Early Launch Anti-Malware (ELAM) operator.
Information: This operator has one information input – a blacklist of known malicious operators that must be prevented from launching as boot start operators during system startup. The blacklist, situated at the registry key below, is determined by Sophos user-space threat detection logic when it identifies a malicious operator. During the subsequent boot cycle, SophosEL.sys ensures that this operator is not loaded.
| Input | Description | Security |
| HKLMSYSTEMCurrentControlSetServicesSophos ELAMConfig | Blacklist of known malicious operators | DACLs; Sophos Tamper Protected |
Client options: Customers can configure rectification and permitted items in the Threat Protection policy from Sophos Central.
Supplementary precautions: Any Microsoft or Sophos-approved operator is exempted from sanitation/blockage.
Operation: SophosED.sys (Endpoint Defense) is a boot start operator, initiated during ELAM processing and before the loading of various other kernel operators, the initialization of Windows user-space, and the mounting of the system drive. It holds three primary responsibilities:
- Offering tamper protection for the Sophos establishment and arrangement
- Evidencing system activity events to Sophos user-spacecomponents for safeguarding and detection
- Documenting system activity events at a low level to the Sophos Event Journals for subsequent forensic investigation and examination
Inputs: As SophosED.sys initializes prior to the availability of the filesystem, its complete setup is delivered through its service key. It is important to note that all inputs listed below are within HKLMSYSTEMCurrentControlSetServicesSophos Endpoint Defense.
Filter driver altitudes inputs
Operating as a Mini-Filter driver in Windows, SophosED.sys is assigned multiple altitudes (an exclusive identifier determining a driver’s placement in the ‘stack’ of drivers, with ‘lower’ drivers positioned closer to the underlying hardware) that have been specifically assigned and sanctioned by Microsoft.
| Input | Description | Safeguarding |
| HKLMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseInstances | Several altitudes assigned by Microsoft | DACLs; Secure from Sophos Tampering |
Tamper Protection inputs
The setup of Sophos Tamper Protection is a collaborative effort involving customer policies, Sophos feature flags, and digitally signed manifests embedded within the agent.
| Input | Description | Safeguarding |
| HKLMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseTamperProtectionConfig | Customer policy (On/Off, configuration password*) | DACLs; Secure from Sophos Tampering |
| HKLMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseTamperProtectionComponents
HKLMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseTamperProtectionServices |
Manifest of secured keys, directories, services, etc. | Digitally signed; validated by driver prior to loading |
* The configuration password undergoes hashing via PBKDF2-SHA512 with the addition of a salt
System Activity Events inputs
The configuration flexibility of the Sophos Central Threat Protection policy is transcribed by user-space processes from SophosED.sys registry keys for accessibility upon driver initialization.
| Input | Description | Safeguarding |
| HKLMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseScanningConfig | Customer policy (On/Off, exclusions, etc.) | DACLs; Secure from Sophos Tampering |
| HKLMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseEndpointFlags | Various Sophos feature flags | DACLs; Secure from Sophos Tampering |
Event Journal inputs
| Input | Description | Safeguarding |
| HLKMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseEventJournalConfig | Customer policy (exclusions, disk limits) | DACLs; Secure from Sophos Tampering |
| HLKMSYSTEMCurrentControlSetServicesSophos Endpoint DefenseEventJournalFeatures | Presence of a subkey with a DWORD value Enabled=1 indicates activation of event journals | DACLs; Secure from Sophos Tampering |
Customer options: Customers have the ability to set disk limits and manage exclusions within the Sophos Central Threat Protection policy.
Additional measures: The ability to configure various parameters dynamically during runtime is facilitated by Sophos user-space processes in instances where a driver facility is present (determined by a blend of Customer Policy and Sophos flags):
- An assortment of mitigations to be applied per process
- Specification of events for activation or deactivation per process
- Defining the duration the driver should await a response from user-space (or whether it should be an asynchronous notification).
What it carries out: Sntp.sys (Sophos Network Threat Protection) is a kernel driver that subscribes to various Windows Filtering Platform events for interception and potential modification of network flow data. Distinct filters and callouts are enlisted based on the features authorized by Sophos Central Threat Protection and Web Control policies.
Inputs: Configuration of features is transmitted to the driver from one or more user-mode processes as enumerated below:
- SophosNtpService.exe
- SophosNetFilter.exe
- SophosIPS.exe
- SSPService.exe
Interactions between user-space processes and the driver are facilitated through the Windows Driver Framework, utilizing IOCTLs, Read, and Write operations. Bidirectional communication with the driver is safeguarded, permitting only connections from authorized and genuine Sophos processes.
Customer options: The filter driver intercepts traffic from browser and non-browser processes based on the policies formulated within Sophos Central. Processing of intercepted traffic is conducted in user-space by SophosNetFilter.exe and SophosIPS.exe, which may relay modified content back to the driver (e.g., for displaying a block page for malicious content).
Additional measures: Customers have the capability to append specific sites to their allow or block list in Sophos Central.
What it carries out: Hmpalert.sys enforces Sophos CryptoGuard, responsible for the identification and prevention of file encryption in bulk by ransomware. Additionally, it configures the application of exploit mitigations as processes are executed.
Inputs: Hmpalert.sys encompasses varied inputs, inclusive of distinct registry subkeys and IOCTLS.
| Input | Description | Safeguarding |
| HKLMSYSTEMCurrentControlSetServiceshmpalert | Software setup | DACLs; Secure from Sophos Tampering |
| HKLM SYSTEMCurrentControlSetServiceshmpalertConfig | Customer policy | DACLs; Secure from Sophos Tampering |
| HKLM SYSTEMCurrentControlSetServicesSophos Endpoint DefenseEndpointFlags | Various Sophos feature flags | DACLs; Secure from Sophos Tampering |
Customer options: Customers can designate the activation or deactivation of exploit mitigations and manage exclusions within the Sophos Central Threat Protection policy.
Additional measures: N/A
What it carries out: SophosZtnaTap.sys functions as a Sophos-manufactured OpenVPN TAP driver. When a customer deploys the Sophos Zero Trust Network Access (ZTNA) agent, the driver captures DNS lookups for managed applications and reroutes traffic for these applications to the appropriate Sophos ZTNA gateways. Configuration of ZTNA applications and gateways is governed by Sophos Central policies and stored in the registry.
Inputs: The inputs to SophosZtnaTap.sys are facilitated via a registry subkey.
| Input | Description | Safeguarding |
| HKLMSOFTWARESophosManagementPolicyNetworkPerimeter | Access Control Lists; Sophos Secure Tamper-proof |
Client choices: End-users have the ability to oversee their ZTNA-protected applications and gateways through Sophos Central.
Added precautions: Not Applicable
The Sophos CryptoGuard has been warding off mass encryption on fixed disks for more than ten years. In the latest version of Intercept X (2024.1.1), a novel functionality, CryptoGuard ExFAT, was introduced to extend this safeguard to ExFAT partitions (commonly found on detachable USB drives).
The development and trial of CryptoGuard ExFAT spanned from September 2023 to March 2024. This attribute was safeguarded by the marker ‘hmpa.cryptoguard-exfat.available.’
Beginning March 22, 2024, Sophos Engineering internally executed the software with the indicator activated (our ‘Dogfood release’).
Intercept X version 2024.1.1 was initially launched internally at Sophos, following which it was gradually rolled out to clients using our phased software distribution method, spanning May 21, 2024 to June 6, 2024. During this phase, the attribute remained inactive for all users except Sophos engineers.
The flag ‘hmpa.cryptoguard-exfat.available’ was activated using our phased flag activation process, between June 10, 2024 to June 26, 2024.
Clients have the option to pick a particular software version (Endpoint Software Management: Fixed-term maintenance, Long-term maintenance). By doing so, the software and indicators are locked until a different software bundle is chosen. Users who opt for the ‘Sophos-recommended’ choice receive updated software at intervals. Aside from software deployments, they also gain gradual activation of indicators for fresh features in the software, similar to a conventional software release. Sophos has refined this process to enhance reliability and prevent activating new functionalities globally for all customers.
Kernel drivers are crucial to the Intercept X Enhanced package – and to resilient Windows endpoint security in general – yet we recognize that working in kernel-space entails inherent risks.
This post delves into the kernel drivers in Intercept X Enhanced (as of release 2024.02), their functions, their authentication process, their inputs, the control users have over their administration, and the supplementary protections we’ve implemented – such as gradual, phased rollouts of new features and exemptions to minimize the prospects of disruption.
Even though no precaution can completely eliminate risks, we aim to provide a comprehensive understanding of our drivers for transparency, elucidating how we approach the intricate challenge of safeguarding our clientele from threats in the safest manner possible.