
ESET Research
Researchers at ESET came upon a new exploit in Telegram for Android, allowing the sneaky distribution of hazardous files masked as videos
22 Jul 2024
•
,
6 min. read

Research specialists at ESET unearthed a groundbreaking exploit focused on Telegram for Android, which surfaced for sale at an undisclosed price in an underground post dated June 6th, 2024. Through this exploit, dubbed EvilVideo, malevolent entities could disseminate harmful Android payloads via Telegram channels, groups, and chats, camouflaging them as multimedia files.
Having obtained an example of the exploit, we delved deeper into its analysis and promptly reported our findings to Telegram on June 26th, 2024. Subsequently, on July 11th, they released an update rectifying the vulnerability in Telegram versions 10.14.5 and above.
Shown in Figure 1 is a video providing a demonstration and an elucidation of the EvilVideo vulnerability.
Figure 1. Elucidation of the EvilVideo vulnerability
Main highlights of the blog post:
- On June 26th, 2024, an advertisement for a zero-day exploit targeting Telegram for Android was discovered in an underground forum.
- The vulnerability exploited by the exploit was named EvilVideo, and the findings were promptly reported to Telegram; their team acted swiftly to patch it on July 11th, 2024.
- EvilVideo facilitated malevolent entities in transmitting harmful payloads disguised as video files in outdated Telegram versions for Android.
- The exploit was only functional on Telegram versions for Android 10.14.4 and earlier.
Unearthing
We stumbled upon the exploit being marketed for purchase in an underground forum, as depicted in Figure 2.
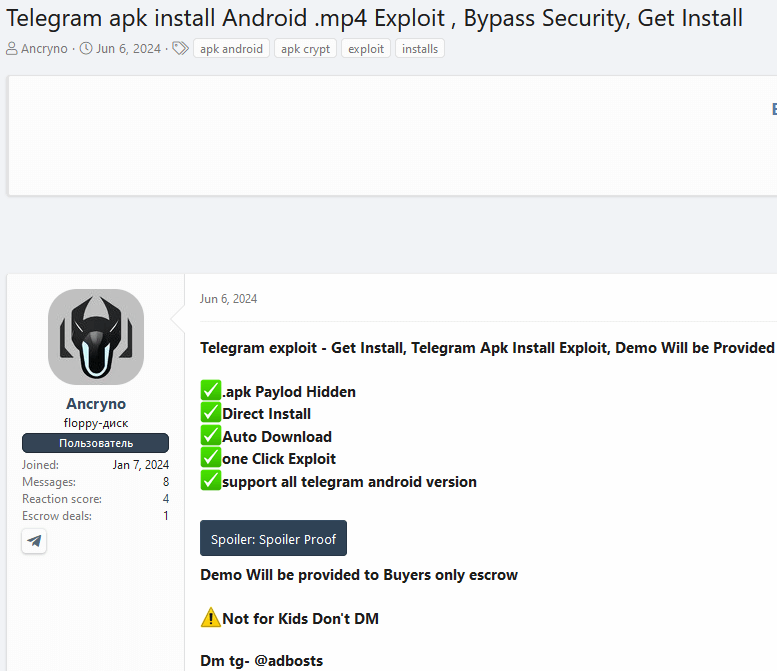
In the post, the vendor exhibited screenshots and a video demonstrating the exploit in action within a public Telegram channel. We succeeded in pinpointing the channel of interest, where the exploit remained accessible. This allowed us to acquire the payload for testing.
Evaluation
Our evaluation of the exploit divulged its compatibility with Telegram versions 10.14.4 and prior. Our conjecture is that the distinctive payload was most likely artfully crafted utilizing the Telegram API, which grants developers the ability to upload specifically designed multimedia files programmatically to Telegram chats or channels.
The exploit seems to hinge on the exploit agent’s capability to create a payload that exhibits an Android app as a multimedia preview rather than a binary attachment. Once distributed in a chat, the malicious payload adopts the guise of a 30-second video (see Figure 3).
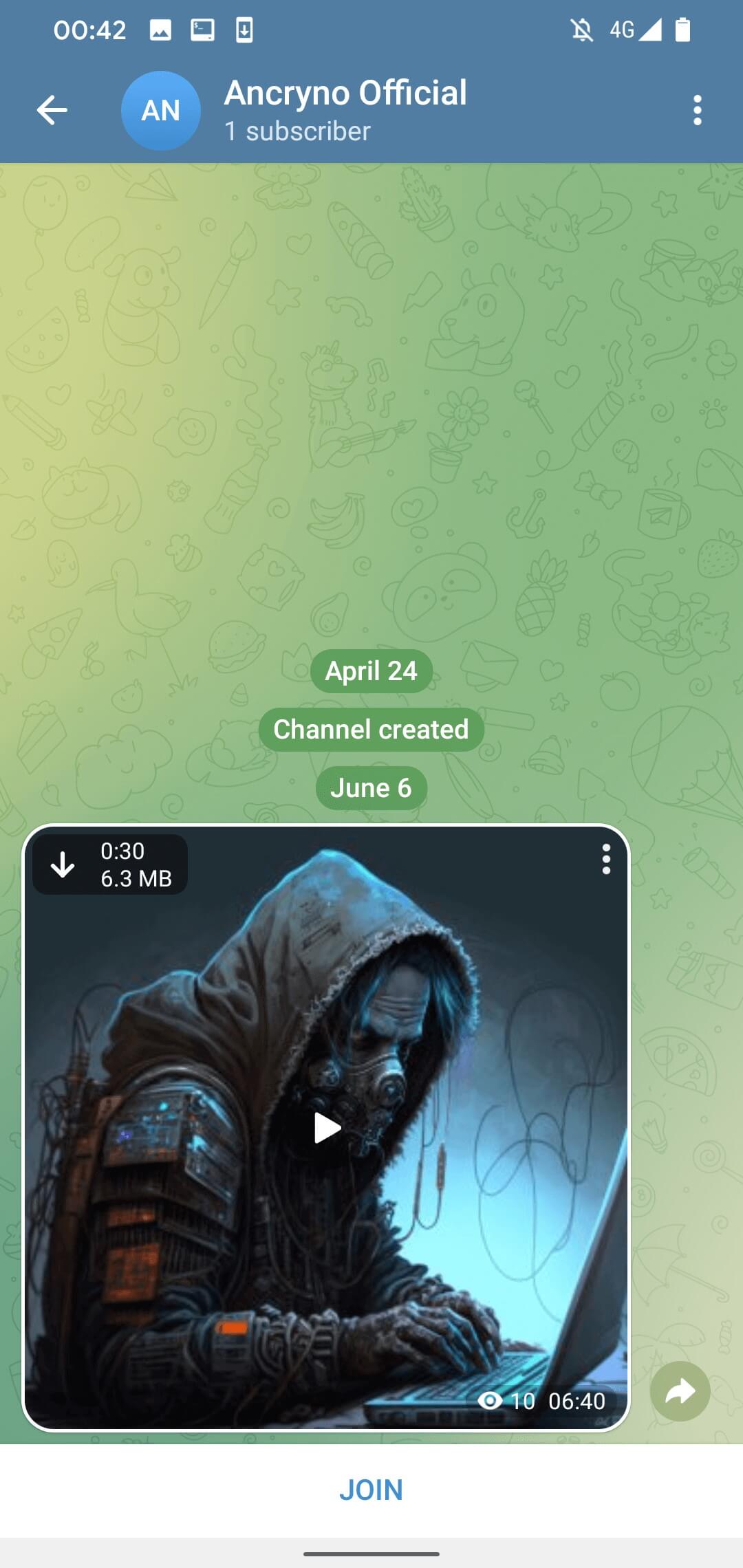
By default, multimedia files received via Telegram are configured to auto-download. This implies that users with this feature enabled would trigger the automatic download of the malevolent payload upon accessing”);
A Windows executable could be utilized instead of the Android APK, and it would still be recognized as a multimedia file, rendering the exploit ineffective.

Threat actor
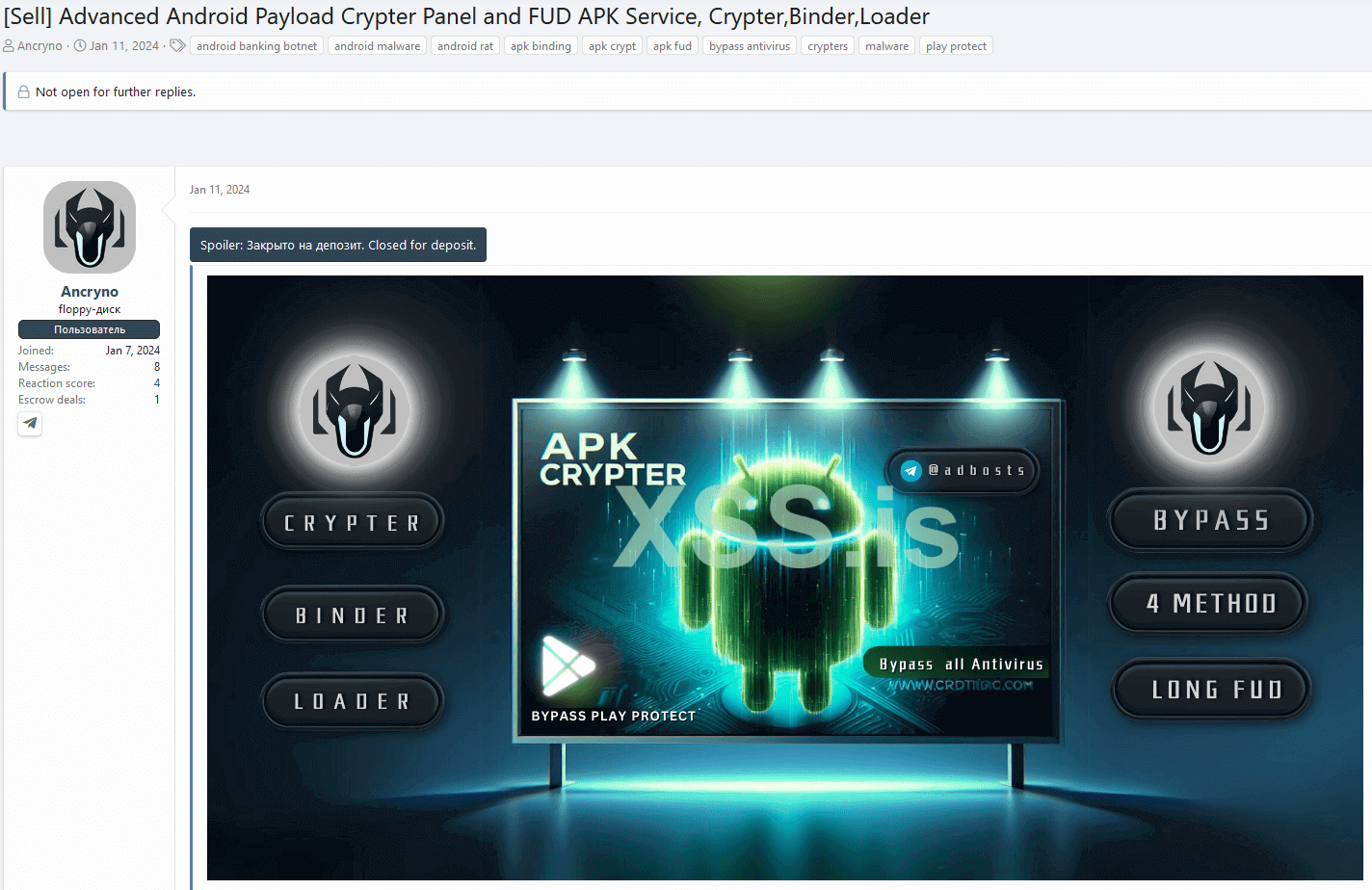
Although limited information is available about the threat actor, we were able to uncover another dubious service they offer based on the Telegram handle provided in their forum post. Apart from the exploit, they have also been promoting an Android cryptor-as-a-service in the same underground forum, boasting full undetectability (FUD) since January 11th, 2024. See Figure 8 for the forum post.
Vulnerability report
Following the identification of the EvilVideo vulnerability on June 26th, 2024, we adhered to our coordinated disclosure policy and notified Telegram without receiving an initial response. Subsequently, upon lodging another report on July 4th, Telegram promptly reached out to confirm that their team was investigating EvilVideo. A fix was deployed with the release of version 10.14.5 on July 11th, with notification communicated via email.
The vulnerability impacted all Android versions of Telegram up to 10.14.4 but has since been patched in version 10.14.5. As confirmed, the chat multimedia preview now correctly identifies the shared file as an application (see Figure 9) rather than a video.

Conclusion
We uncovered a zero-day exploit targeting Telegram for Android being auctioned on an underground forum. This exploit enabled the dissemination of malicious payloads camouflaged as multimedia files through Telegram chats. If a user attempted to view the alleged video, they would be prompted to install an external app, which was actually delivering the malicious payload. Fortunately, after our report to Telegram, the vulnerability was addressed by July 11th, 2024.
For any queries regarding our published research on WeLiveSecurity, reach out to us at threatintel@eset.comESET Research offers private APT intelligence reports and data feeds. Contact us for inquiries related to this service through the ESET Threat Intelligence page.
Indicators of Compromise
A detailed list of Indicators of Compromise (IoCs) and samples is available in our GitHub repository.
Files
|
SHA-1 |
Filename |
Detection |
Description |
|
F159886DCF9021F41EAA |
Teating.apk |
Android/Spy.SpyMax.T |
EvilVideo payload. |
Network
|
IP |
Domain |
Hosting provider |
First seen |
Details |
|
183.83.172[.]232 |
infinityhackscharan. |
Administrator Beam Cable System |
2024‑07‑16 |
C&C server of EvilVideo payload. |
MITRE ATT&CK techniques
The content of this table was crafted using version 15 of the MITRE ATT&CK mobile techniques.
|
Tactic |
ID |
Name |
Description |
|
Initial Access |
Exploitation for Initial Access |
The EvilVideo vulnerability can be abused by Android malware to achieve initial device access. |
|
|
Execution |
Exploitation for Client Execution |
The EvilVideo vulnerability tricks the victim into installing a malicious app that impersonates a multimedia file. |









