Frauds
Your unassuming phone number holds more value than you might realize. Discover how it could end up in the wrong hands – and ways to safeguard it from scammers.
15 Jul 2024
•
,
7 min. read

How can scammers easily deceive someone for financial gain without revealing their identity?
Could it revolve around acquiring their credit card details, possibly through digital skimming or infiltrating a database containing sensitive personal data? While effective, such methods can be resource-intensive and demand technical expertise.
What about obtaining payment information via fraudulent websites? This approach may seem plausible, but imitating legitimate sites (and email addresses to “spread the word”) may not suit everyone. The chances are high that these strategies will be identified promptly by those adept in security or be foiled by security measures.
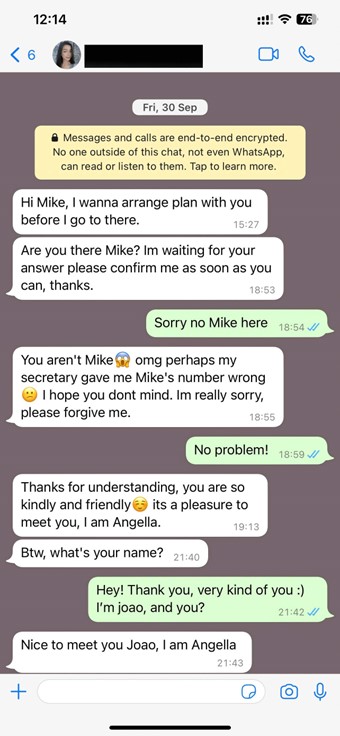
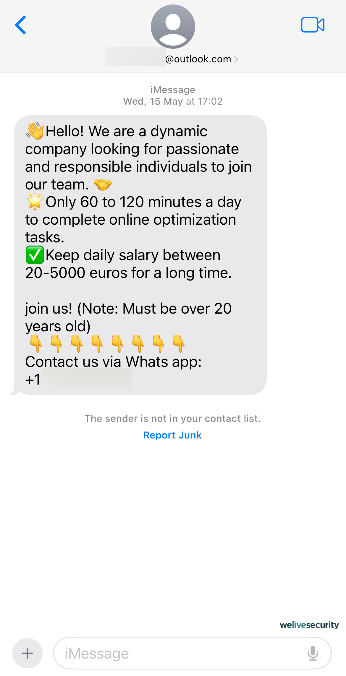
Instead, malicious individuals are embracing highly scalable operations that hinge on sophisticated social manipulation techniques and involve minimal operational costs. Through voice phishing (also known as vishing) and message scams (smishing), these operations have evolved into a lucrative scam call-center industry valued at billions of dollars.
Initially, these schemes may not necessitate specialized or technical expertise. Additionally, a single individual (often a target of human trafficking) can simultaneously entrap numerous unsuspecting victims in various forms of fraud. These encompass pig butchering, cryptocurrency schemes, romance scams, and tech support fraud, each weaving a captivating tale that exploits elements of our humanity.
Hey there! Can you hear me?
Picture receiving a call purportedly from your bank, asserting that your account has been compromised and urging you to divulge sensitive information to safeguard your funds. The urgency in the voice of the bank’s “representative” might compel you to disclose your private data. However, this individual might not represent your bank – or might not even exist. It could simply be a fabricated voice that sounds convincingly human.
This scenario isn’t uncommon, and cautionary anecdotes from recent times are plentiful. In 2019, a CEO fell victim to a nearly US$250,000 scam orchestrated using a realistic voice deepfake of their parent firm’s leader. Similarly, a finance professional was duped via a deepfake video call in 2024, costing their company US$25 million.
Artificial Intelligence, the facilitator
Thanks to advancements in AI voice replication and translation technologies, vishing and smishing have become more accessible. In fact, ESET Global Cybersecurity Advisor Jake Moore demonstrated how effortless it is for anyone to create a realistic deepfake impersonation of another person – even someone familiar to you. Witnessing and hearing no longer guarantee authenticity.
AI is diminishing the entry thresholds for new malevolent actors, serving as a versatile tool for data aggregation, automating mundane tasks, and expanding their global footprint. Consequently, phishing exploits utilizing AI-generated voices and text are likely to become more prevalent.
In a related development, a recent study by Enea unveiled a 1,265% surge in phishing incidents since the introduction of ChatGPT in November 2022, underscoring the potential of large language models to empower such illicit activities.
Who are you, what’s your contact?
According to Consumer Reports’ research from 2022, individuals are increasingly mindful of their privacy. Approximately 75% of the survey participants expressed some level of concern regarding the privacy of data gathered online, including telephone numbers, which serve as valuable assets for identification and marketing.
Now that we’ve moved well beyond the era of printed directories, how does the symbiosis between phone numbers and marketing operate?
Reflect on thisexemplary instance: a devoted enthusiast of baseball inserted tickets into the checkout feature of a specific application but failed to finalize the transaction. Shortly after exiting the application, he was contacted via telephone and presented with a discounted offer for the tickets. Naturally, he was puzzled as he had not recollected sharing his phone number with the application. So, how did the application come into possession of his number?
The solution lies in tracking. Certain trackers have the capability to gather precise details from a webpage. Thus, once you input your phone number into a form, a tracker may detect and store it for the purpose of crafting what is commonly referred to as personalized content and experience. There exists a complete business model recognized as “data brokerage,” and unfortunately, a security breach is not a prerequisite for the exposure of this information to the public.
Surveillance, data vendors, and disclosures
Data vendors harvest your personal details from various origins, including publicly available sources (government-issued licenses/registrations), commercial entities (business affiliates such as credit card issuers or retail establishments), and by monitoring your online engagements (e.g., activities on social platforms, ad clicks, etc.), subsequently vending this data to others.
Nevertheless, you might be pondering: how do fraudsters obtain the phone numbers of other individuals?
The more companies, websites, and applications you divulge your private information to, the more intricate your individualized “marketing profile” becomes. This heightens your vulnerability to data disclosures, as data vendors themselves can encounter security breaches. A data vendor could potentially vend your information to unauthorized parties, including malicious entities.
Nonetheless, data vendors or breaches affecting them are not the sole sources of phone numbers for scammers. Here are various methods through which malicious actors can access your phone number:
- Accessible sources: Social media platforms or digital job marketplaces may publicly exhibit your phone number as a mode of establishing a connection. If your privacy settings are improperly configured or you are unaware of the repercussions of publicizing your phone number on your social media profile, your number could be accessible to anyone, including an automated web scraper.
- Compromised accounts: Numerous online services necessitate your phone number, whether for identity verification, placing an order, or serving as an authentication element. If your accounts are compromised due to weak passwords or if any of your online service providers undergo a data breach, your number could easily be exposed.
- Automated dialers: Automated dialers randomly ring numbers, and once you answer the call, you may be subjected to a fraudulent scheme. At times, these automated dialers call merely to affirm that the number is operational, allowing it to be appended to a roster of targets.
- Correspondence: Inspect any recent packages delivered to you – these often display your address visibly on the envelope/box. However, in specific scenarios, they may also exhibit your email or phone number. What if an individual pilfered one of your packages or delved into your recycling repository? Given that data breaches frequently encompass the same information, this situation can be perilous and serve as a foundation for further misuse.
As exemplified by a large-scale disclosure affecting phone numbers, AT&T recently disclosed that millions of customers’ call and text message records from the latter part of 2022 were compromised in an extensive data breach. Nearly all customers of the firm and individuals utilizing the cellular network have had their numbers, call durations, and the quantity of call interactions exposed. Despite claims that call and text content were not part of the exposed data, customer names and numbers can still be easily linked, as reported by CNN.
Allegedly, blame is to be assigned to a third-party cloud platform that was accessed by a malicious actor. Interestingly, this same platform has experienced several instances of massive data breaches associated with it in recent times.
Securing your phone number
So, how can you safeguard yourself and your number? Here are some recommendations:
- Exercise vigilance against phishing. Refrain from responding to unsolicited communications/calls from foreign numbers, avoid clicking on unfamiliar links in your emails/messages, and remember to maintain composure and deliberate before responding to urgent situations that may be an attempt to deceive you.
- Consult your service provider regarding their SIM security protocols. They might offer card locks as a defense against SIM swapping, for instance, or supplementary account security layers to combat scams such as call forwarding.
- Fortify your accounts with two-step verification, preferably utilizing dedicated security keys, applications, or biometrics instead of SMS-based verification. The latter can be intercepted by malicious actors relatively easily. Extend this practice to service provider accounts as well.
- Exercise caution before furnishing your phone number to a website. While having it as an additional recovery option for your diverse applications may be practical, other alternatives such as secondary emails/authenticators may provide a more secure substitute.
- Consider employing a prepaid SIM card or a Voice over Internet Protocol (VoIP) service instead of your regular phone number for online transactions.
- Implement a mobile security solution featuring call filtering and ensure that third-party cookies in your web browser are disabled. Explore additional privacy-enhancing tools and technologies.
In a world increasingly reliant on online data retention, it is highly improbable that your number remains unrecorded by a third party somewhere. The AT&T incident underscores the inadequacies of relying solely on the security measures of your carrier. However, this does not imply that you should perpetually harbor a state of paranoia.
Instead, it underscores the necessity of adhering to good cybersecurity practices and exhibiting awareness of your online data. Diligence remains paramount, particularly in light of the ramifications of this emerging, AI-driven (under)world.





