Frauds
Your modest phone number holds more worth than you might realize. Discover how it could land in dishonest hands – and how you can aid in keeping it away from fraudsters.
15 Jul 2024
•
,
7 min. read

What could be considered as one of the simplest approaches to defraud someone out of their money anonymously?
Could it be related to appropriating their credit card information, possibly through digital skimming or gaining illicit access to a repository of delicate personal data? Despite being effective, these techniques might demand abundant resources and necessitate a certain level of technical expertise.
How about seizing payment details via counterfeit websites? While this tactic could fit the bill, mimicking authentic websites (and email addresses for “word-of-mouth” promotion) may not suit everyone. There is also a high likelihood that such schemes will be promptly identified by security-conscious individuals or obstructed by security measures.
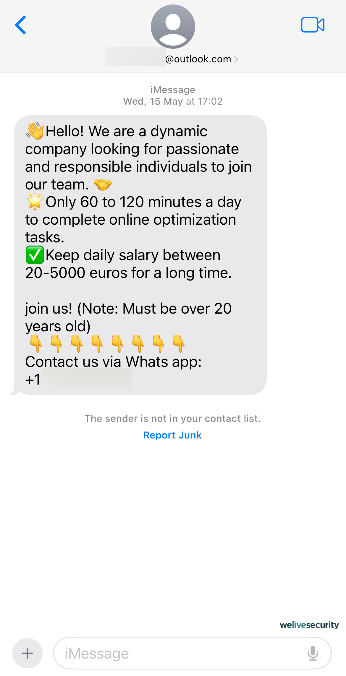
Instead, malicious entities are resorting to highly scalable operations that rely on sophisticated social manipulation techniques and involve minimal costs. By using voice phishing (commonly known as vishing) and message scams (smishing), these operations have evolved into a scam call-center industry valued in billions of dollars.
Initially, these stratagems might not necessitate specialized or technical expertise. Furthermore, a solitary individual (frequently a target of human trafficking) can ensnare numerous unwitting victims concurrently in diverse forms of deceit. These often encompass pig butchering, cryptocurrency schemes, romance scams, and tech support fraud, each spinning a captivating narrative and preying on certain aspects of our humanity.
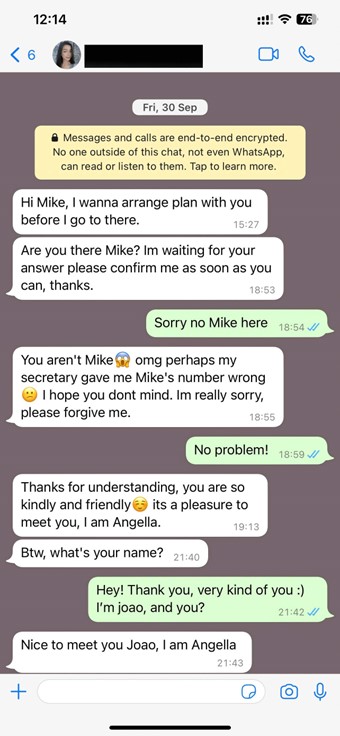
Hey, can you hear me?
Picture this: you receive a call purportedly from your bank alerting you that your account has been compromised, and in order to safeguard your funds, you are required to disclose your sensitive information to them. The sense of urgency in the voice of the bank’s “staff member” might be adequate to coerce you into revealing your sensitive details. The issue here is that this individual may not represent your bank – or perhaps not even exist at all. It could just be synthetically-generated speech, yet still sounding entirely genuine.
Instances of this nature are not unusual, and cautionary anecdotes from recent years are plentiful. For instance, in 2019, a CEO fell victim to a scam, being bilked out of nearly US$250,000 by a convincing voice deepfake impersonating their parent company’s CEO. Similarly, a finance professional was duped via a deepfake video call in 2024, resulting in US$25 million loss for their organization.
Artificial Intelligence, the facilitator
With the contemporary AI voice cloning and translation capabilities, vishing and smishing have become simpler than ever. Indeed, ESET Global Cybersecurity Advisor Jake Moore demonstrated how effortlessly anyone can generate a believable deepfake rendition of another person – even someone familiar to you. Observation and audition are no longer synonymous with certainty.
AI is reducing the threshold for entry among new adversaries, acting as a versatile tool for data collection, automatizing mundane tasks, and expanding their global outreach. Consequently, phishing endeavors utilizing AI-generated voices and text are anticipated to become more prevalent.
In that vein, a recent study by Enea documented a 1,265% surge in phishing schemes subsequent to the debut of ChatGPT in November 2022, underscoring the potential of extensive language models to propel such malicious pursuits.
What’s your appellation, what’s your digit?
Evident from Consumer Reports study from 2022, individuals are growing increasingly mindful of their privacy compared to earlier times. About 75% of the survey’s participants exhibited at least some level of concern regarding the privacy of their online-captured data, including telephone numbers, owing to their usefulness in both identification and marketing.
But now that we have surpassed the era of the Yellow Pages, how does this amalgamation of telephone numbers and promotional activities function?
Contemplate thisexemplary case: a baseball enthusiast added tickets to a specialized app’s cart yet failed to finalize the transaction. Subsequently, shortly after exiting the application, he was contacted by phone with an offer of a discount on the tickets. Naturally, he was confused as he did not recall providing his phone number to the application. How then was his number acquired?
The response is – through tracking. Some trackers have the capability to gather specific details from a webpage. Thus, after you have entered your phone number in a form, a tracker could identify and retain it to generate what is commonly referred to as personalized content and user experience. There exists an entire business model known as “data brokering”, and unfortunately, data does not necessarily need to be breached to become public.
Tracking, information brokers, and breaches
Information brokers acquire your personal data from various sources, including publicly available channels (governmental licenses/registrations), commercial resources (collaborators such as credit card issuers or retailers), and by monitoring your online interactions (engagement on social media, ad clicks, etc.), before selling this data to other entities.
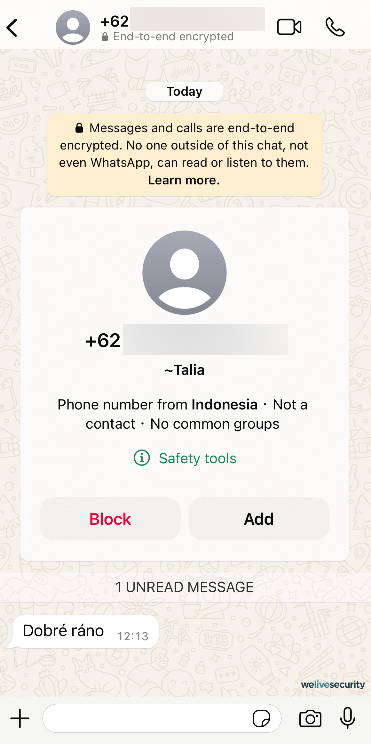
However, you may be contemplating how scammers manage to acquire phone numbers belonging to other individuals?
The more companies, websites, and apps you disclose your personal particulars to, the more intricate your personal “marketing profile” becomes. Consequently, this elevates your vulnerability to data breaches, as data brokers themselves can encounter security lapses. A data broker might also vend your details to third parties, potentially including malicious entities.
Nonetheless, data brokers or breaches involving them are not the only sources from which scammers obtain phone numbers. Here are several other techniques through which criminals can acquire your phone number:
- Open sources: Platforms such as social media or online job portals may display your phone number for networking purposes. Should your privacy settings be configured inadequately or if you are unaware of the repercussions of disclosing your phone number in your social media profile, your number could be accessible to anyone, including an AI-based web scraper.
- Hijacked accounts: Several online services mandate your phone number for verification, ordering products, or authentication. If your accounts are compromised due to weak passwords or if one of your online service providers undergoes a data breach, your number could be leaked swiftly.
- Robocallers: Automatic calling systems dial random numbers, and upon answering, you may be targeted by a fraudster. At times, these robocallers phone to validate the activity of a number in order to include it in their target list.
- Correspondence: Review your recent postal deliveries – these often present your address visibly on the parcel, and in certain cases, they may also inscribe your email or phone number. Imagine if someone pilfered one of your deliveries or sifted through your discarded items. Given that data breaches generally entail the same details, this scenario can be highly perilous and serve as grounds for further exploitation.
An extensive breach related to phone numbers, AT&T recently disclosed that millions of customers’ call and text logs from the latter half of 2022 were exposed due to a massive data spill. Nearly all of the company’s clients and individuals using the cellular network have had their numbers, call durations, and the frequency of call interactions exposed. While chat and text content purportedly did not form part of the leaked data, client names and numbers could still be effortlessly correlated, as detailed by CNN.
The responsibility appears to lie with a third-party cloud service, which a hostile actor had infiltrated. Coincidentally, this same service has encountered multiple instances of significant breaches in recent years.
Securing your phone number
So, how can you safeguard both yourself and your number? Here are some recommendations:
- Beware of phishing attempts. Refrain from responding to unsolicited calls/messages from foreign numbers, abstain from clicking random links in your emails/messages, and maintain composure, contemplating before acting in response to seemingly urgent situations, as these are typical strategies employed by malefactors.
- Inquire with your service provider about their SIM protection measures. They might offer features such as card locks to ward off SIM swapping, alongside additional layers of account security to fend off scams like call forwarding.
- Strengthen your accounts with dual-factor authentication, preferably utilizing specialized security keys, applications, or biometrics instead of SMS-based verification. The latter method is susceptible to interception by malicious actors. Extend the same protection to your service provider accounts as well.
- Exercise caution before sharing your phone number on a website. Although it may serve as an additional recovery option for your various applications, alternate methods such as secondary emails or authenticators could offer a more secure substitute.
- For online transactions, contemplate using a prepaid SIM card or a VoIP service instead of your ordinary phone number.
- Employ a mobile security application with call screening capabilities, ensure that third-party cookies in your web browser are blocked, and explore other privacy-enhancing tools and technologies.
In a world increasingly reliant on digital record-keeping, the likelihood of your number not being retained by a third party somewhere is minimal. Furthermore, as evidenced by the AT&T breach incident, entrusting your carrier’s security measures can be fraught with challenges. However, this does not imply that you should harbor a perpetual sense of paranoia.
Conversely, it underscores the importance of adhering to proper cyber hygiene and being conscious of your online data. Vigilance remains paramount, particularly when contemplating the repercussions of this emerging, AI-driven underworld.








