
What follows is a compilation of ransomware encounters by 592 IT/cybersecurity executives in the financial sector over the past year, providing fresh perspectives on the challenges they confront today.
The most recent yearly report by Sophos delves into the real-world ransomware incidents faced by financial services institutions, exploring the complete journey from frequency of attacks and underlying causes to operational repercussions and business results.
The latest publication uncovers new focal points for examination within the industry, such as a comparison between ransom demands and payments, as well as the frequency with which financial entities receive assistance from law enforcement agencies to address breaches.
Access the full report to delve into the comprehensive findings.
Consistent Attack Rates with Heightened Recovery Costs
Last year saw ransomware impacting 65% of financial establishments, mirroring the 64% figure from 2023, indicating a trajectory higher than the preceding two years.
Following ransomware incidents, 90% of financial institutions reported cybercriminal attempts to infiltrate their backups. Approximately 48% of these attempts succeeded, marking one of the lowest backup compromise rates across various sectors.
49% of ransomware assaults on financial entities led to data encryption, showing a significant decline from the 81% in 2023. The financial sector exhibited the lowest data encryption rate across all sectors and the most successful prevention of data encryption post-attack.
The average recovery cost for financial entities in the aftermath of ransomware attacks in 2024 stood at $2.58M, surging from the $2.23M recorded in 2023.
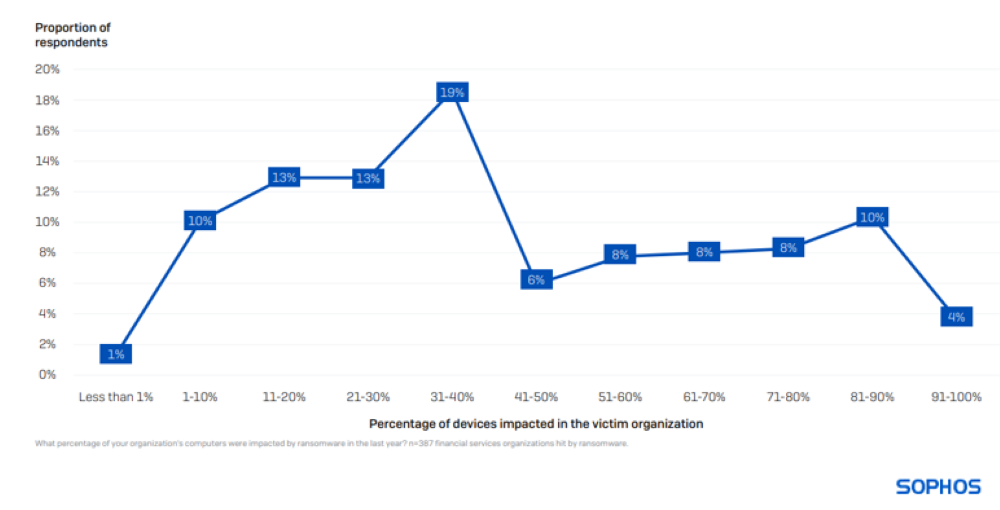
Scope of Impact on Devices during Ransomware Intrusions
On average, ransomware incidents affected 43% of computers within financial organizations, slightly below the cross-sectoral average of 49%. Instances of entire environments being encrypted remained scarce, with only 4% of entities reporting 91% or more devices compromised.

Increasing Trend of Ransom Payments in Financial Services
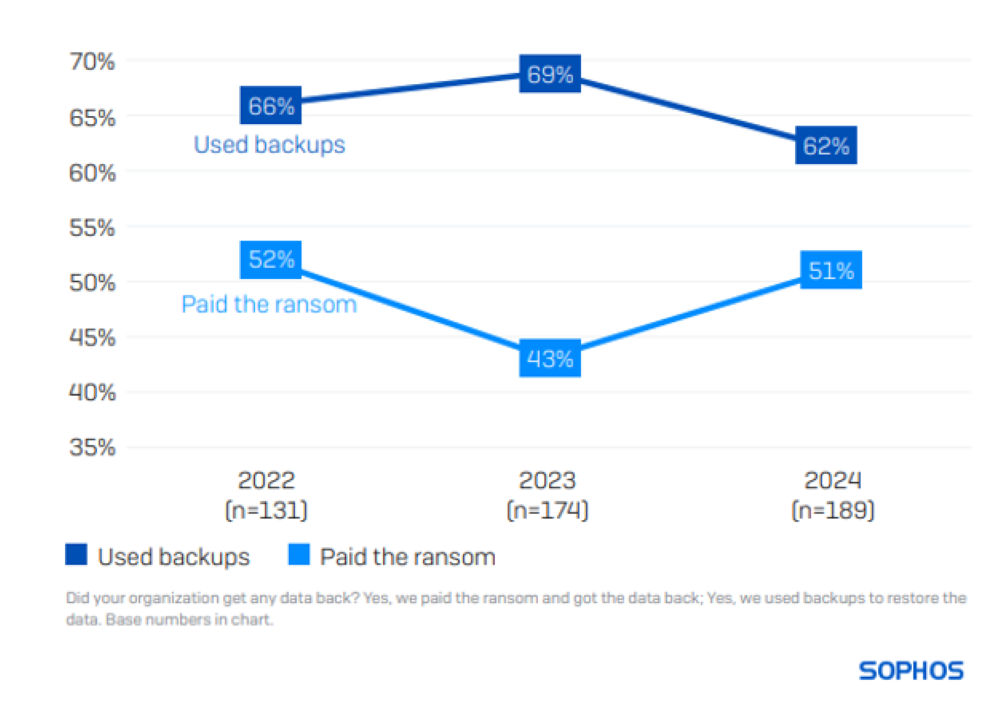
When facing encrypted data, 62% of financial institutions opted to restore using backups, while 51% resorted to paying the ransom for data retrieval. Globally, 68% relied on backups and 56% made ransom payments in similar circumstances.
Insights spanning three years in the financial sector highlight a narrowing gap between the utilization of backups and paying ransoms. In 2023, 69% employed backups, while 43% resorted to ransom payments to recover encrypted data post-attack.
An intriguing shift over the past year is the rise in victims employing multiple strategies for data retrieval (e.g., combining ransom payments and backup usage). In this year’s examination, 37% of financial institutions that encountered data encryption reported resorting to more than one approach, reflecting more than double the percentage seen in 2023 (16%).
Minimal Compliance with Initial Ransom Demands among Financial Entities
Among financial sector respondents who paid ransom, the median sum revealed an 18-fold increase over a year, rising from $109,000 to $2M.
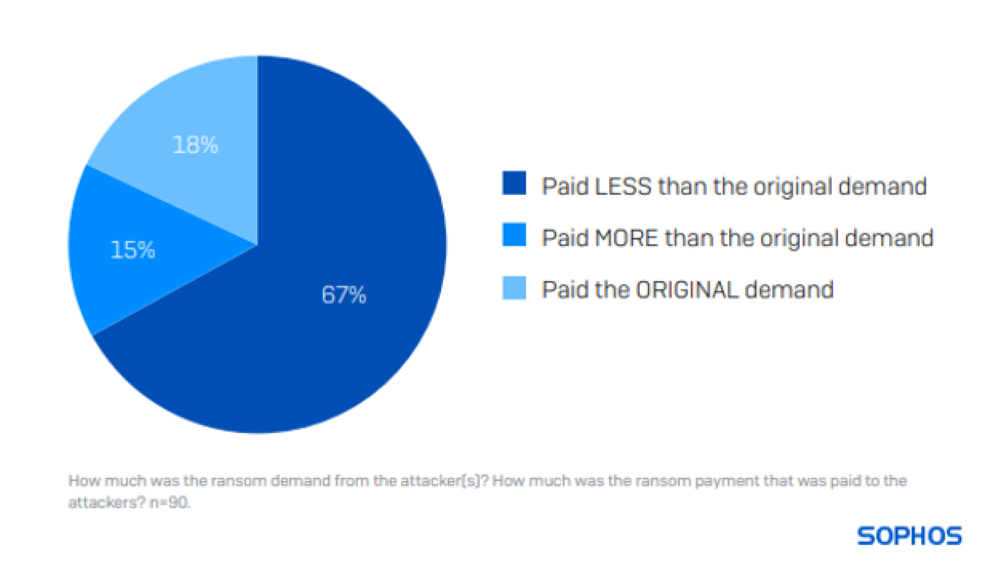
Merely 18% settled the initial ransom request. A majority (67%) paid less than demanded, with 15% surpassing the original figure. On average, financial organizations paid out 75% of the initial ransom sum initially demanded by threat actors.
For deeper insights into ransom payments and other related topics, download the comprehensive report.
Survey Methodology Information
Based on a survey conducted by Sophos, these insights stem from a vendor-neutral study involving 5,000 IT/cybersecurity leaders across 14 nations in the Americas, EMEA, and Asia Pacific, including 592 from the financial sector. All participants represent organizations with staff ranging from 100 to 5,000 employees. Fieldwork was executed by research specialist Vanson Bourne between January and February 2024, with responders drawing from experiences within the previous year.






