
Recent analysis by Sophos concerning the tangible ransomware events in retail establishments ventures into the inclusive victim progression, encompassing attack frequency, core reasons, operational repercussions, and business aftermaths.
This year’s document offers fresh realms of examination, encompassing a contrast of ransom requests versus payouts and the frequency with which retail entities seek aid from law enforcement agencies in counteracting assaults.
Access the complete report to delve into the exhaustive discoveries.
Reduction in Assault Incidents, But Enhanced Recovery Costs
The tally of retail entities reporting ransomware incidents was 45% last year. This demonstrates a prominent and heartening decrease from the 69% and 77% ransomware occurrences in 2023 and 2022, respectively.

92% of retail organizations impacted by ransomware in the preceding year indicated that cybercriminals attempted to infiltrate their backups during the assault. Among these endeavors, 47% proved successful.
56% of ransomware episodes targeting retail entities led to data encryption, marking a substantial decline from the 71% recorded in 2023 and 68% in 2022. The data encryption rate in the retail sector was markedly lower than the universal multi-sector average of 70% and the least across all sectors except financial services (49%).
Retail noted the second-highest data extortion incidence (5%) in conjunction with financial services, where the data wasn’t encrypted but was held for a ransom.
The average expense for retail establishments in bouncing back from a ransomware incident stood at $2.73M in 2024, escalating from the $1.85M documented in 2023.
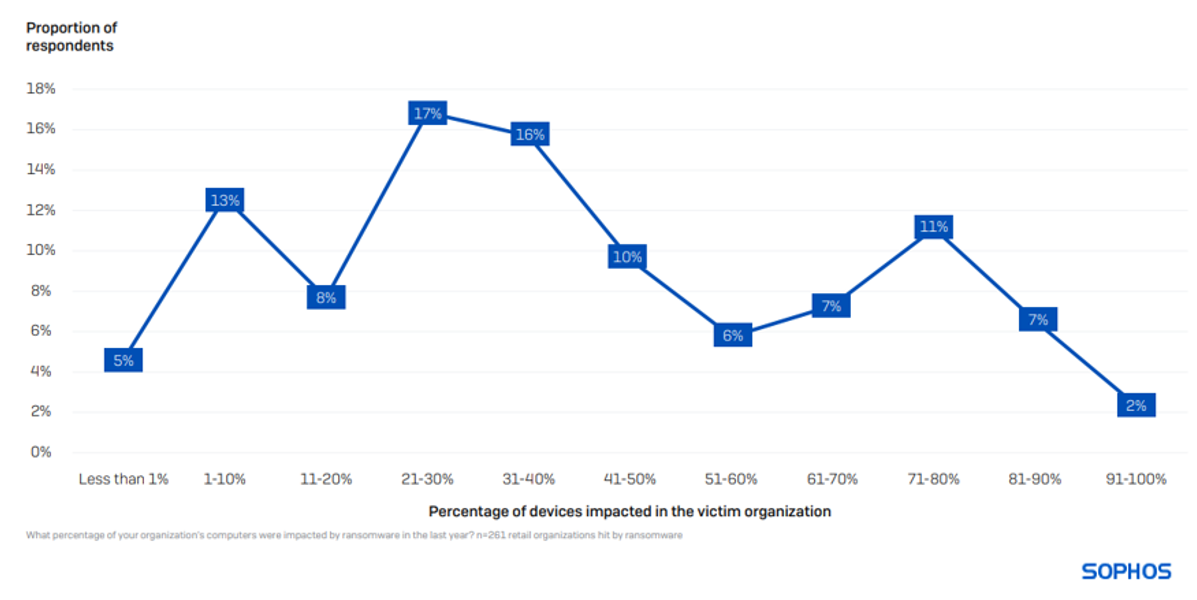
Assorted Devices Affected in a Ransomware Event
On average, 40% of computing systems in retail undergo the ramifications of a ransomware attack. Encountering a full environment encryption is exceedingly uncommon, with solely 2% of organizations indicating that 91% or more of their gadgets suffered impairment.
Increasing Affinity of Retail Firms to Fulfill Ransom Demands
While 66% of retail establishments restored their encrypted information through backups, 60% opted to remit the ransom for data recovery. The deployment of backups in retail firms has seen a minor decline for the consecutive second year, yet the escalating inclination of the sector to pay the ransom is more disconcerting, having witnessed substantial growth over the past year.

An apparent transformation over the preceding year is the upsurge in victims employing varied techniques to recover encrypted data (e.g., paying the ransom and utilizing backups). This year’s evaluation reveals that over a third of retail entities (39%) that underwent data encryption leveraged more than one methodology, surpassing twice the rate registered in 2023 (16%).
Minimal Adherence to Initial Ransom Amounts in Retail Environments
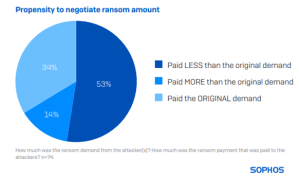 78 respondents from retail organizations that complied with ransom demands furnished details of the actual sum paid, exposing a median expenditure decline of 68% from $3M to $950K over the past year.
78 respondents from retail organizations that complied with ransom demands furnished details of the actual sum paid, exposing a median expenditure decline of 68% from $3M to $950K over the past year.
Just a third (34%) of respondents confirmed that their payment mirrored the original request. 53% remitted less than the initial appeal, while only 14% paid more.
Download the extensive report for further revelations on ransom remittances and a myriad of other domains.
Study Background
The dossier hinges on insights derived from an autonomous, vendor-neutral inquiry initiated by Sophos among 5,000 IT/cybersecurity frontrunners across 14 nations in the Americas, EMEA, and Asia Pacific, encompassing 577 from the retail realm. All survey takers represent establishments with staff ranging from 100 to 5,000 individuals. The assessment, conducted by research authority Vanson Bourne between January and February 2024, requested input predicated on their encounters throughout the earlier year.






