Insights
Dropbox adds end-to-end encryption for team folders
There’s also an integration between Dropbox Replay and Microsoft OneDrive, which lets users pull files from Microsoft’s file storage platform into the video and audio...
TransUnion transforms its business model with IT
At the core of its strategy is the mountain of data that TransUnion has acquired — along with more than 25 companies — over decades....
Android versions: A living history from 1.0 to 15
The Android 1.0 home screen and its rudimentary web browser (not yet called Chrome). Cupcake was all about the widgets. Android’s universal search box made...
The unspoken obnoxiousness of Google’s Gemini improvements
The Gemini on Android reality The truth is that using Gemini as an assistant on Android, to borrow a phrase from my wise progeny, still...
M&A action is gaining momentum, are your cloud security leaders prepared?
As we near the halfway point of the year, organizations are under tremendous pressure to grow businesses across all industries. It’s no secret: bottom lines...
CIOs eager to scale AI despite difficulty demonstrating ROI, survey finds
Security and AI Among the IT leaders taking a cautious approach to AI is Saurabh Gugnani, the global head of cyber defense and application security...
Trending News
What makes Starmus unique? A Q&A with award-winning filmmaker Todd Miller
Video The director of the Apollo 11 movie shares his views about the role of technology in addressing pressing global challenges as well as why...
How technology drives progress: A Q&A with Nobel laureate Michel Mayor
Join us as we speak to the Nobel Prize-winning astronomer Michel Mayor about the intersection of technology and scientific discovery, the art of making science...
The vision behind Starmus: A Q&A with the festival’s co-founder Garik Israelian
Video Dr. Israelian talks about Starmus's vision and mission, the importance of inspiring and engaging audiences, and the strong sense of community within the Starmus...
Protecting yourself after a medical data breach – Week in security with Tony Anscombe
What are the risks and consequences of having your health data exposed and what are the steps to take if it happens to you? (more…)
The many faces of impersonation fraud: Spot an imposter before it’s too late
Scams What are some of the most common giveaway signs that the person behind the screen or on the other end of the line isn’t...
The ABCs of how online ads can impact children’s well-being
Kids Online From promoting questionable content to posing security risks, inappropriate ads present multiple dangers for children. Here’s how to help them stay safe. Imogen...

 Cryptocurrencies and cybercrime: A critical intermingling
Cryptocurrencies and cybercrime: A critical intermingling  Kaiser Permanente data breach may have impacted 13.4 million patients
Kaiser Permanente data breach may have impacted 13.4 million patients 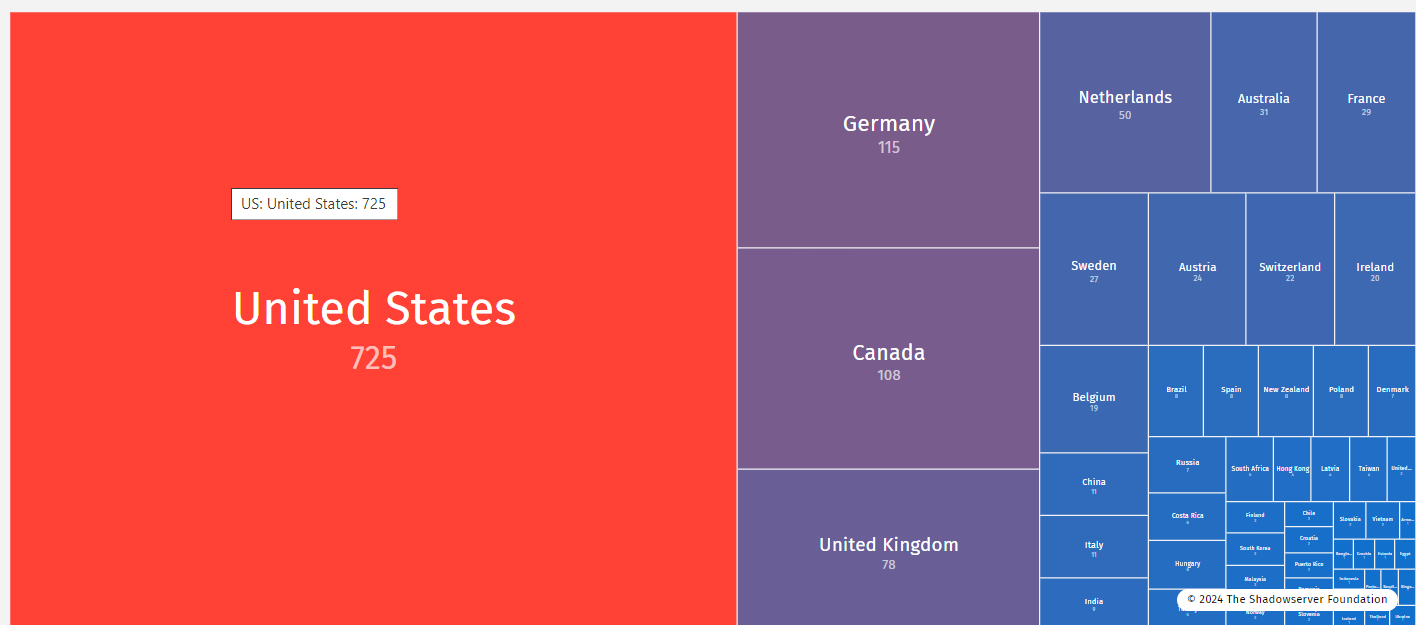 +1,400 CrushFTP servers vulnerable to CVE-2024-4040
+1,400 CrushFTP servers vulnerable to CVE-2024-4040  Dropbox adds end-to-end encryption for team folders
Dropbox adds end-to-end encryption for team folders