Year: 2025
How crooks use IT to enable cargo theft
The average stolen shipment value doubled to $336,787, up from $168,448 in Q3 2024, “clear evidence that cargo thieves are...
Denmark and Norway investigate Yutong bus security flaw amid rising tech fears
Denmark and Norway investigate Yutong bus security flaw amid rising tech fears Pierluigi Paganini November 10, 2025 Denmark and Norway...
MCP for Technical Professionals: A Comprehensive Guide to Understanding and Implementing the Model Context Protocol
Table of Contents Foundation & Context Core Concepts Deep Dive MCP vs APIs – The Technical Reality Security &...
HYPR and Yubico Deepen Partnership to Secure and Scale Passkey Deployment Through Automated Identity Verification
For years, HYPR and Yubico have stood shoulder to shoulder in the mission to eliminate passwords and improve identity...
Microsoft product roadmap hints at ‘Agentic Users’ with their own M365 licenses
“Our expectation is that it will provide a combination of user-like access to Microsoft 365 services on a monthly/annual/3-annual fee...
IBM Infrastructure: Continuous Risk & Compliance
Learn all about AI-powered visibility, telemetry, and proactive security across mainframe, cloud, containers, and enterprise workloads. (more…)
Generative AI: The Double-Edged Sword of Cybersecurity
The AI hacking era is here – and it’s reshaping the human risk landscape as we know it. With...
Crypto-less Crypto Investment Scams: A California Case
My readers will know by now that I am addicted to PACER – the Public Access to Court Electronic...
New Attacks Against Secure Enclaves
Encryption can protect data at rest and data in transit, but does nothing for data in use. What we...
Agentic AI in Cybersecurity: Beyond Triage to Strategic Threat Hunting
Agentic AI in Cybersecurity: Beyond Triage to Strategic Threat Hunting Pierluigi Paganini November 10, 2025 With a 4M cybersecurity worker...
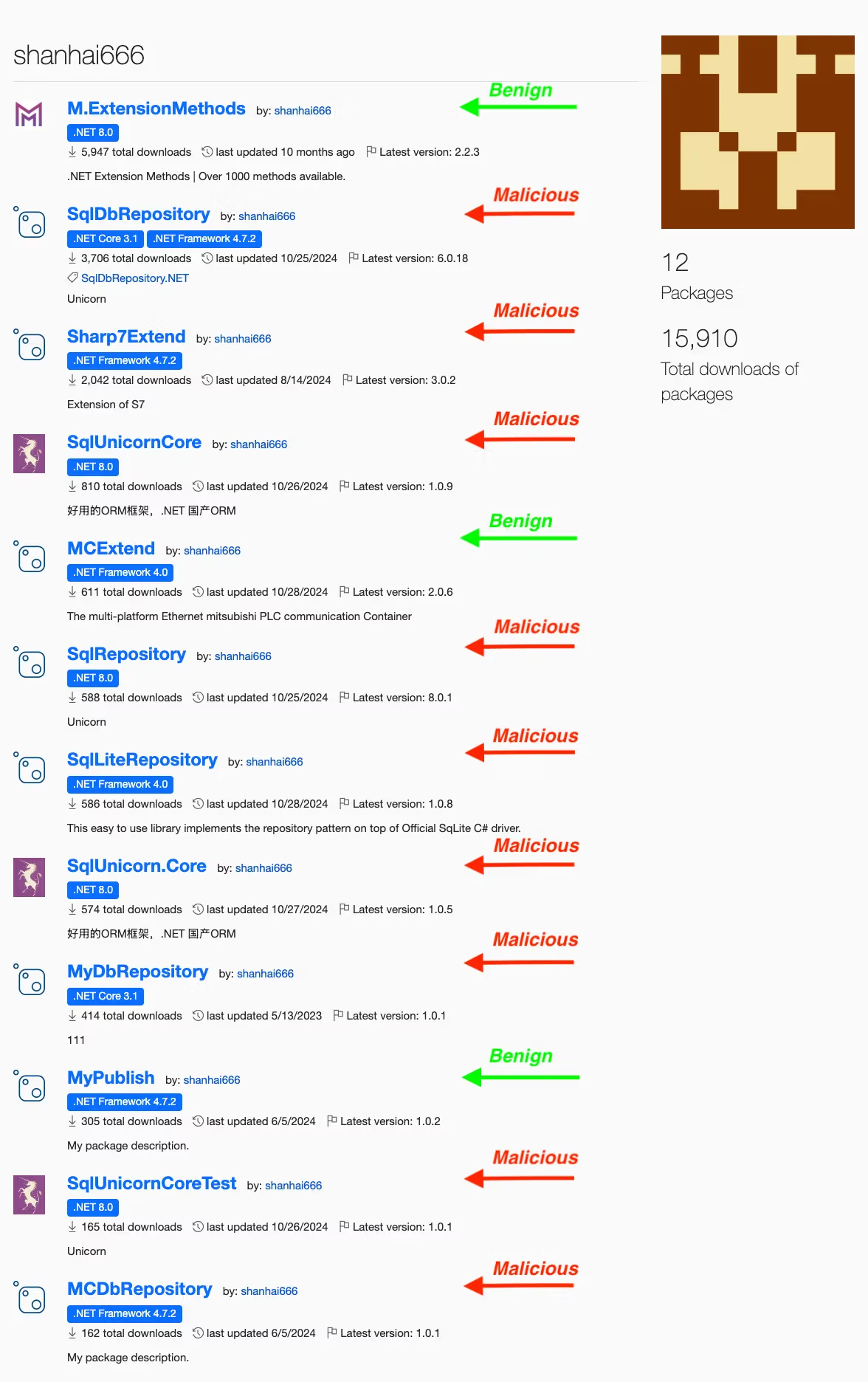
Nine NuGet packages disrupt DBs and industrial systems with time-delayed payloads
Nine NuGet packages disrupt DBs and industrial systems with time-delayed payloads Pierluigi Paganini November 10, 2025 Nine NuGet packages by...
Hack halts Dutch broadcaster, forcing radio hosts back to LPs
A Dutch TV and radio broadcaster has found itself at the mercy of cybercriminals after suffering a cyber attack, and...
The Mosaic Effect: Why AI Is Breaking Enterprise Access Control
Security has always been a puzzle of fragments. For decades, analysts have warned about the mosaic effect: The risk...
⚡ Weekly Recap: Hyper-V Malware, Malicious AI Bots, RDP Exploits, WhatsApp Lockdown and More
Cyber threats didn't slow down last week—and attackers are getting smarter. We're seeing malware hidden in virtual machines, side-channel leaks...




.jpg?width=672&height=215&name=Yubico-1%20(1).jpg)