2024 Uncovered: The Distressing Condition of Australian Data Breaches

The Office of the Australian Information Commissioner’s most recent Notifiable Data Breaches Report unveiled a swift increase nationwide in notifiable data breaches in the initial half of 2024 — a 9% boost when contrasted with the last half of 2023 and the highest quantity of notifications since 2020.
The report, unleashed in September, evidenced that recent data breaches, containing the beach of medical prescription service MediSecure impacting 12.9 million Australians, have resulted in a robust response from the OAIC. The agency cautioned that it is embracing a stricter standpoint on data privacy and breaches, accentuating that organizations should give precedence to privacy in their data methodologies.
Which industries encountered the most data breaches?
The OAIC has publicized statistical information on data breach notifications since the establishment of the Notifiable Data Breaches scheme in Australia in 2018. The most recent report disclosed:
- A sum of 527 notifications transpired from January to June 2024, signifying a 9% upsurge when compared with the 485 notifications received from July to December 2023.
- The most recent six-month period observed the highest quantity of notifications received since July to December 2020, during the depths of the global COVID-19 pandemic.
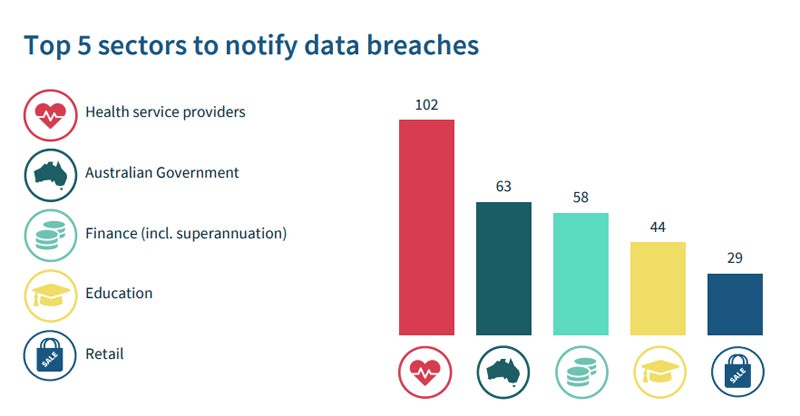
- The top five sectors undergoing data breaches were health service providers (102 breaches), the Australian Government (63), finance (58), education (44), and retail (29).
- Malicious or criminal attacks, both external and internal, were the origin of 67% of all data breaches, followed by human error (30%) and system failures (3%).
- Malicious or criminal attacks encompassed cyber incidents (57%), social engineering/impersonation (27%), theft of paperwork or data storage (8%), and rogue employee/insider threats (8%).
- The majority of breaches reported (63%) involved 100 people or fewer, but there were eight large-scale breaches impacting over 100,000 people, including Australia’s “largest ever” MediSecure breach.
SEE: Australian organizations facing highest rate of data breaches
Cyber incidents reign over malicious and criminal attacks in Australia
Cyber incidents persist as a prevalent source of data breaches, constituting 38% of total breaches. Cyber incidents were defined as those involving phishing, ransomware, compromised or stolen credentials (technique unknown), brute-force attacks, hacking, and malware — excluding social engineering-style attacks.
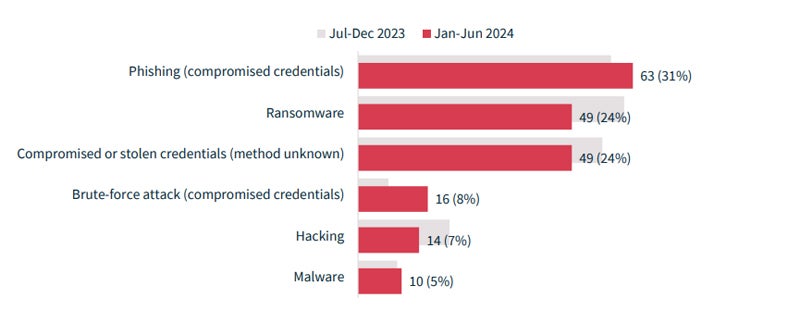
Among the diverse malicious or criminal attacks, cyber incidents impacted individuals the most. The average of 107,123 individuals were impacted by the 201 cyber incidents, while an average of 4,709 individuals were affected by incidents arising from rogue employees or insider threats.
In the report, Australian Privacy Commissioner Carly Kind mentioned that the enduring prevalence of cyber incidents in the data breach totals reported to the OAIC emerged “as our increasing reliance on digital tools and online services exposes our details more frequently to malicious cyber actors.”
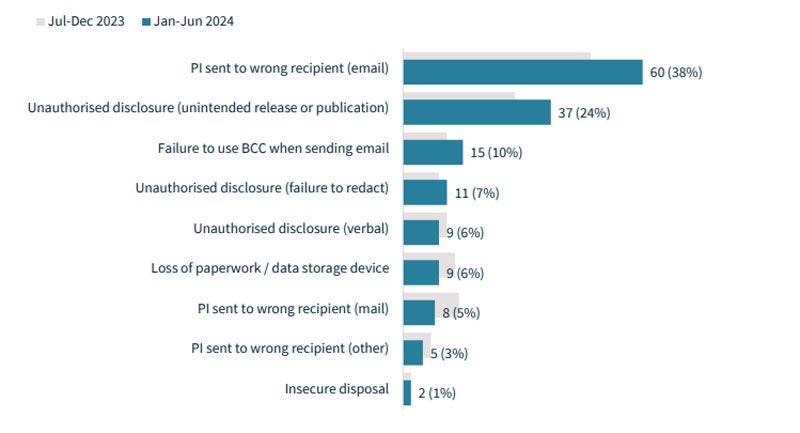
Nevertheless, human error still represents 30% of notifiable data breaches. The primary categories of human error were:
- Personally identifiable information dispatched to the incorrect email recipient (38%).
- Unsanctioned disclosure of information, or unintended release or publication (24%).
- Abstaining from using the Bcc (Blind copy) option when sending email (10%).
Spike in data breaches positionsAustralian Government entities under the limelight
As per the observations made by the OAIC, the Australian Government registered the second-highest count of data breaches across all industries, marking its peak ranking till date, even though it has previously been listed in the top five compromised sectors. The report highlights:
- There were 63 reported data breaches by Government agencies from January to June 2024, constituting 12% of all data breach notifications in Australia.
- Government bodies were responsible for the largest number of social engineering or impersonation-related data breaches, accounting for 42% of such occurrences. According to the OAIC, these breaches typically revolved around a threat actor pretending to be a customer in order to obtain access to an account using valid credentials.
- Furthermore, the Government displayed a slower response time, with the largest segment (87%) of notifications where the agency detected the incident over 30 days after its occurrence, and 78% of Government notifications were initiated more than 30 days after the agency was made aware of the incident.
SEE: Is the public sector in Australia equipped to handle a major cyber security incident?
Suggestions to prevent data breaches
Incessantly, cybersecurity experts stress to organizations that a significant number of data breaches or cyber attacks could be averted by integrating fundamental cybersecurity protocols. The OAIC presented various suggestions based on the trends evident in data breaches.
Alleviating cyber threats
The primary recommendation put forth by the OAIC was to enforce multi-factor authentication as a priority to combat cyber threats, or adopt robust password management policies and procedures in the absence of MFA. Additionally, the agency suggested:
- Implementing layered security controls to evade a single-point failure.
- Enforcing different levels of access to data based on roles and responsibilities.
- Utilizing security monitoring to identify, address, and report incidents or anomalous activities.
The OAIC referred to frameworks like Australia’s Essential Eight, the Information Security Manual from the Australian Signals Directorate, the Cyber Security Framework from the National Institute of Standards and Technology in the U.S., as well as the ISO 27001 and ISO 27002 information security management standards from the International Organisation for Standardisation, as guiding measures for enhancing practices.
Risks associated with extended supply chains
According to the OAIC, several significant data breaches originate from compromises within the supply chain, such as the incident affecting MediSecure and another scenario involving Outabox. The agency highlighted that the outsourcing of personal information management to third parties continues to pose a prevalent risk.
The OAIC recommended that companies evaluate the risks associated with outsourcing the handling of personal data right from the initial stages of procurement, including when engaging cloud providers. It emphasized the need for organizations to establish a robust supplier risk management framework, alongside reinforcing security measures.
Tackling the human element
The OAIC stressed that individuals constitute a substantial threat to the privacy practices’ integrity. These threats encompass breaches stemming from human errors or employees falling victim to phishing attacks.
The agency recommended that organizations employ technical measures to minimize errors, and highlighted the importance of educating staff to ensure they comprehend their privacy and security obligations. Furthermore, it suggested prioritizing staff training in secure information handling practices.
Misconfigurations in cloud-based data storage
The OAIC highlighted that certain organizations are “neglecting” cloud security aspects during their digital transformation. Instances of data breaches in the period occurred due to the misconfiguration of security settings by an Australian entity owing to human oversight, thus exposing personal data to unauthorized access or public disclosure.
The OAIC underlined that organizations should not assume the entire responsibility of cloud security lies with the provider. It underscored the importance of prioritizing cloud security and management, emphasizing the adoption of measures such as secure access controls via MFA, IP access controls, and encryption.



